Many enterprises find that by careful consideration of the default behavior roles, a widely published pre-shared key, and the Default Rule, they can meet their security requirements without extra effort. This model is quite workable and provides adequate security. It is also simple to deploy and maintain.
Some enterprises may wish to create additional rules that govern communications between two specific systems. There are many reasons that you might want to create new rules to add to the System Policies in a LAN. Usually, you will want to provide an additional layer of security for certain types of communications.
While additional rules are beneficial in certain cases, also consider the extra maintenance that is required. When you create a rule for communications between destination workgroups, you must ensure that these rules are kept updated.
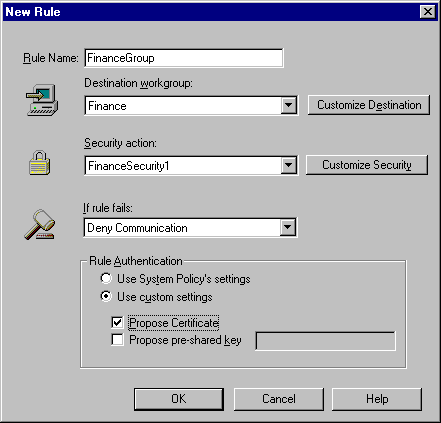
This screen shows a new rule named FinanceGroup. In creating this rule, a new destination workgroup and security action were defined. Additionally, the rule uses a certificate to authenticate the rule instead of the default System Policy settings.

For a discussion about the sample rule shown here, see Customizing Rules.
Copyright © 2000, Intel Corporation. All rights reserved.
Intel Corporation assumes no responsibility for errors or omissions in this document. Nor does Intel make any commitment to update the information contained herein.
* Other product and corporate names may be trademarks of other companies and are used only for explanation and to the owners' benefit, without intent to infringe.