If you have installed Intel® Packet Protect, you have already set up basic security settings for the system. You can view or edit these settings using Intel Packet Protect. Optionally, you can also use the Advanced settings in Intel Packet Protect, if you are familiar with encryption and authentication settings, to configure the security policy that comes with Intel Packet Protect.
The Intel Packet Protect configuration tool displays information about your configuration.
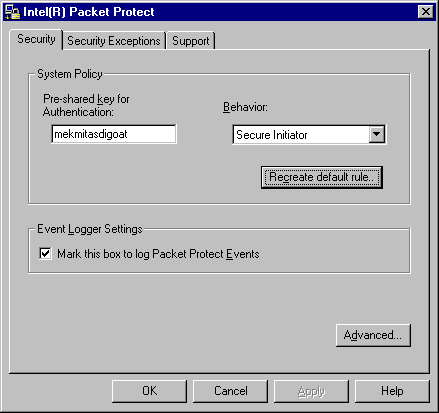
After you install Intel Packet Protect, you can view your basic configuration information on Security tab of the configuration tool. How do I view the Security tab?

When you installed Intel Packet Protect on your system, you entered your pre-shared key and selected a default behavior. These choices are displayed on the Security tab. You can change the settings for these values as well.
Notes:
If you change your Default Behavior, Intel Packet Protect will delete any customized rules that you might have added and replace them with the system's Default Rule. You cannot recover these rules once you have changed behaviors.
Do not change your pre-shared key unless instructed to do so by an administrator. If you enter a pre-shared key that is different from others on your network, you won't be able to communicate securely with them.
Intel Packet Protect can create log entries about problems that may occur. You can click the check box to tell Intel Packet Protect to save these log entries. If you are having trouble running Intel Packet Protect, click this box, as the log entries can provide valuable information for diagnosing and fixing problems with Intel Packet Protect.
Find out more about event logging.
Note: These commands are not available to users who use the Intel® NetStructure™ Policy Manager.
This command restores your Intel Packet Protect settings to their original state when you first installed Intel Packet Protect. When you use this command, you will lose all of your customizations, including additional rules, destination workgroups, and security actions. They cannot be recovered.
Use this command to view the Policy Editor, where you can view and modify the rules in your System Policy or create new rules. See Advanced Security Settings for information about customizing rules.
Copyright © 2000, Intel Corporation. All rights reserved.
Intel Corporation assumes no responsibility for errors or omissions in this document. Nor does Intel make any commitment to update the information contained herein.
* Other product and corporate names may be trademarks of other companies and are used only for explanation and to the owners' benefit, without intent to infringe.